No edit summary |
No edit summary |
||
| Line 55: | Line 55: | ||
} | } | ||
}; | }; | ||
</pre> | |||
==== Findings ==== | |||
Normally you register a callback url to where you want to end up after successful login - the IdentityProvider(IDP) will send an answer to the calling page with a redirect back to us using this url - but with appended ?code=xxxx. However if the request from the IDP lacks referrer or other details the middleware will not understand that this is the call that is the callback from the IDP for a login request. To help the middleware understand that the callback really is a login request and should be treated as such you can send in an redirect url ending with /signin-oidc - this way the middleware cannot miss what it is supposed todo. | |||
Revision as of 15:02, 21 September 2020
OpenId is the protocol to negotiate authentication and get back an access token that your app can verify that it comes from your openId authority so that you may trust the information in the ticket - like the user-email maybe - or some claim that the user is admin or the like.
OpenIdConnect is a standard built on top of OpenId that makes setup much easier.
Even if every OpenId Authority has their own naming on endpoints etc - they can explain what their own way is in the OpenIdConnect contract
https://<OpenIdAuthority>/.well-known/openid-configuration
Debugging
If you have setup issues and need to debug where the issue lies this is a great way:
https://docs.microsoft.com/en-us/azure/databricks/dev-tools/api/latest/aad/app-aad-token
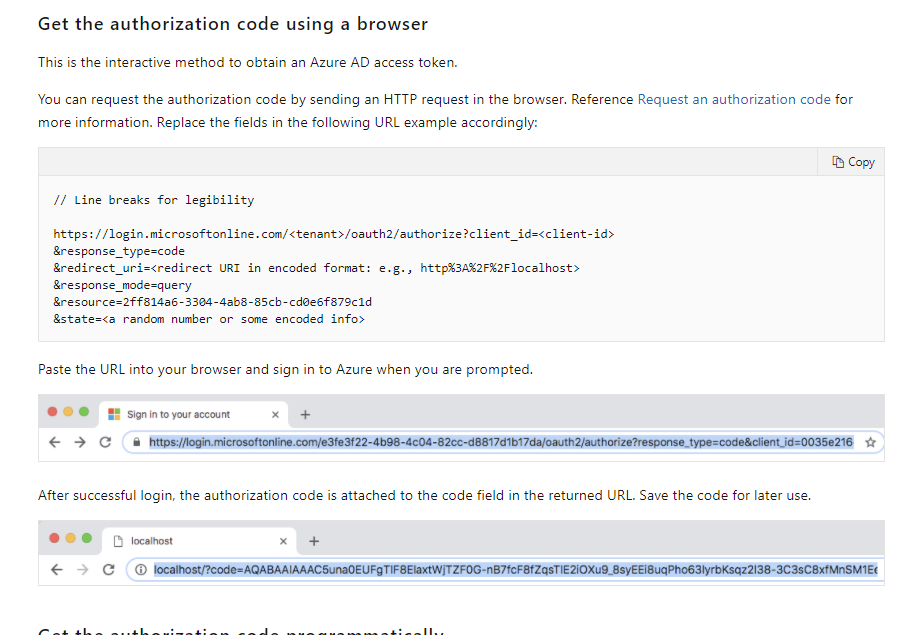
You can use the browser to mimic the calls that will be done. The first call to the OpenIdConnect authority is to get a "one time" code. The Authority will respond with a redirect to the callback url WITH AN APPENDED code.
It is this code you use to get the AccessToken.
This is what we write to the turnkey-log regarding the OpenIdConnect flow:
Notifications = new OpenIdConnectAuthenticationNotifications
{
AuthenticationFailed = context =>
{
Common.CentralLogging("OpenId AuthenticationFailed " + context.Exception.Message);
...
},
AuthorizationCodeReceived = context =>
{
Common.CentralLogging("OpenId AuthorizationCodeReceived0 ");
Common.CentralLogging("OpenId AuthorizationCodeReceived1 " + context.Code);
Common.CentralLogging("OpenId AuthorizationCodeReceived2 " + context.Code + " " + context.AuthenticationTicket.Identity.GetUserName());
...
},
SecurityTokenValidated = context =>
{
Common.CentralLogging("OpenId SecurityTokenValidated " + context.Options.Description);
...
},
RedirectToIdentityProvider = context =>
{
Common.CentralLogging("OpenId RedirectToIdentityProvider1 " + context.Options.RedirectUri);
Common.CentralLogging("OpenId RedirectToIdentityProvider2 " + context.Options.ResponseType);
...
},
SecurityTokenReceived = context =>
{
Common.CentralLogging("OpenId SecurityTokenReceived ");
...
},
MessageReceived = context =>
{
Common.CentralLogging("OpenId MessageReceived ");
...
}
}
};
Findings
Normally you register a callback url to where you want to end up after successful login - the IdentityProvider(IDP) will send an answer to the calling page with a redirect back to us using this url - but with appended ?code=xxxx. However if the request from the IDP lacks referrer or other details the middleware will not understand that this is the call that is the callback from the IDP for a login request. To help the middleware understand that the callback really is a login request and should be treated as such you can send in an redirect url ending with /signin-oidc - this way the middleware cannot miss what it is supposed todo.