(Created page with "First we need oblige that the reasons for restricting access can be manifold. It may be as simple as to avoid confusing a user with too many options at the wrong time in the p...") |
No edit summary |
||
| (12 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
We can set any expression in the Enable expression of an action – | First, we must agree that the reasons for restricting access can be manifold. This may be as simple as avoiding confusing a user with too many options at the wrong time in the process – or it may be as crucial as protecting highly sensitive information from getting into the wrong hands. Any practical Access control is probably based on static information as “users belonging to group Fishermen should not have access to view Treasury”, but also dynamic information as “if a Fisherman has been granted payment but has not collected it yet, he should be able to open the view Treasury”. | ||
Another aspect is that we sometimes want to show that actions are available – but not enabled to you at this particular moment. At other times, we do not even want to show you that a given action exists in the system. These are all common requirements when dealing with access control. Since MDriven solves all user interaction through ViewModels and Actions, it is natural that these are our targets for Access Control. | |||
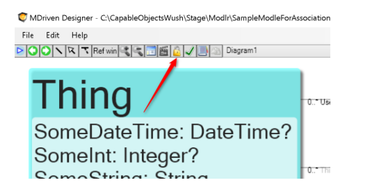
We can set any expression in the Enable expression of an action – this is one way to disable actions. If we have a rule that is the same for many actions, we may consolidate the rule to an AccessGroup: | |||
[[File:Access control system in MDriven 01.png|frameless|365x365px]] | [[File:Access control system in MDriven 01.png|frameless|365x365px]] | ||
| Line 9: | Line 11: | ||
[[File:Accessgroups.png|frameless|429x429px]] | [[File:Accessgroups.png|frameless|429x429px]] | ||
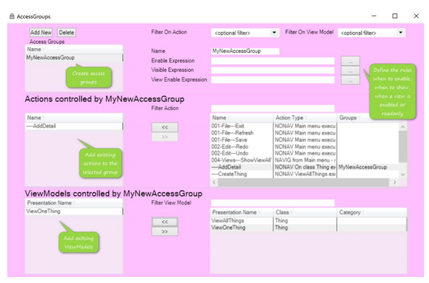
AccessGroups are useful for static rules like checking if the logged-in user is part of the fisherman group: | |||
SysSingleton.oclSingleton.CurrentUser.SysRoles->exists(name=’fisherman’) | SysSingleton.oclSingleton.CurrentUser.SysRoles->exists(name=’fisherman’) | ||
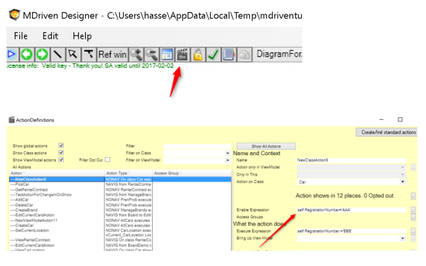
For actions we can set the Enable expression for more precision: | For actions, we can set the Enable expression for more precision: | ||
[[File:Access control system in MDriven.png|frameless|426x426px]] | [[File:Access control system in MDriven.png|frameless|426x426px]] | ||
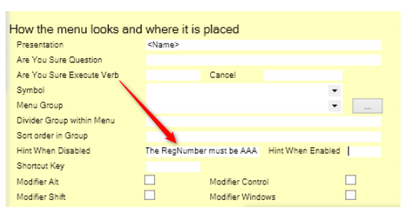
We may also want to give the User a hint as to why the action is disabled. This ability has reduced the support requests a lot in all the projects we have done: | |||
[[File:Access control system in MDriven 03.png|frameless|413x413px]] | [[File:Access control system in MDriven 03.png|frameless|413x413px]] | ||
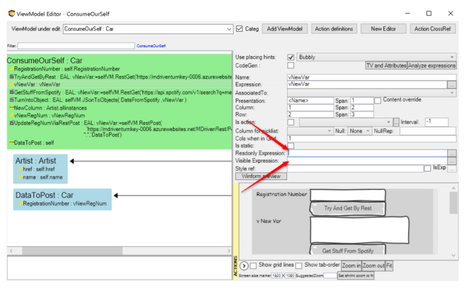
For views | For views, refine the access control per placed widget by setting the ReadOnly expression or/and the Visible expression: | ||
[[File:Access system in MDriven 04.png|frameless|467x467px]] | [[File:Access system in MDriven 04.png|frameless|467x467px]] | ||
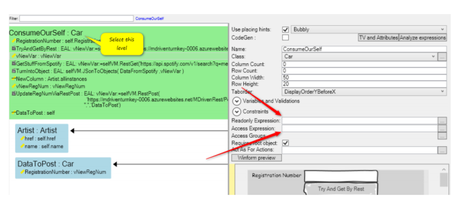
But in views | But in views, you can also work on the whole view: | ||
[[File:Access system in MDriven 05.png|frameless|460x460px]] | |||
Setting the Readonly expression on this level affects all the widgets in the view. Setting the access expression will control if the view is shown at all. | |||
If the view’s Access expression evaluates to false, the system will look for a ViewModel named AccessDenied and if found, will show this instead. If no AccessDenied view is found, then a blank screen will show. To allow you to disable an action that would bring up a view with an access expression evaluating to false given a certain root object, check the result of the Access expression before bringing up the view. Do this with the OCL operator <code>canAccess(vmname):bool</code>. | |||
This enables you to disable actions that will end up showing AccessDenied and stop reports from being created based on a ViewModel and root object that is not allowed based on the Access expression of the ViewModel. | |||
Working with the described levels of expression, you can tailor a perfect-fit access control system that evaluates in the safe realm of your server. All OCL rules use a few OCL operators but mostly names from your model that are probably in a ubiquitous language shared with the security officers of your domain. The transparency and fine-grained control of this access control system is precisely what many organizations need to protect their information and still allow for fast-paced development. | |||
'''NOTE:''' This is the <u>'''last'''</u> chapter of The MDriven Book. | |||
See also: [[Documentation:AccessGroups, InterestGroups and ViewModel-Enable|AccessGroups,_InterestGroups_and_ViewModel-Enable]], [[Documentation:Access_groups|Access_groups]] | |||
[[Category:Advanced]] | |||
[[Category:Access groups]] | |||
[[Category:The MDriven Book]] | |||
Latest revision as of 06:41, 3 April 2024
First, we must agree that the reasons for restricting access can be manifold. This may be as simple as avoiding confusing a user with too many options at the wrong time in the process – or it may be as crucial as protecting highly sensitive information from getting into the wrong hands. Any practical Access control is probably based on static information as “users belonging to group Fishermen should not have access to view Treasury”, but also dynamic information as “if a Fisherman has been granted payment but has not collected it yet, he should be able to open the view Treasury”.
Another aspect is that we sometimes want to show that actions are available – but not enabled to you at this particular moment. At other times, we do not even want to show you that a given action exists in the system. These are all common requirements when dealing with access control. Since MDriven solves all user interaction through ViewModels and Actions, it is natural that these are our targets for Access Control.
We can set any expression in the Enable expression of an action – this is one way to disable actions. If we have a rule that is the same for many actions, we may consolidate the rule to an AccessGroup:
AccessGroups are useful for static rules like checking if the logged-in user is part of the fisherman group:
SysSingleton.oclSingleton.CurrentUser.SysRoles->exists(name=’fisherman’)
For actions, we can set the Enable expression for more precision:
We may also want to give the User a hint as to why the action is disabled. This ability has reduced the support requests a lot in all the projects we have done:
For views, refine the access control per placed widget by setting the ReadOnly expression or/and the Visible expression:
But in views, you can also work on the whole view:
Setting the Readonly expression on this level affects all the widgets in the view. Setting the access expression will control if the view is shown at all.
If the view’s Access expression evaluates to false, the system will look for a ViewModel named AccessDenied and if found, will show this instead. If no AccessDenied view is found, then a blank screen will show. To allow you to disable an action that would bring up a view with an access expression evaluating to false given a certain root object, check the result of the Access expression before bringing up the view. Do this with the OCL operator canAccess(vmname):bool.
This enables you to disable actions that will end up showing AccessDenied and stop reports from being created based on a ViewModel and root object that is not allowed based on the Access expression of the ViewModel.
Working with the described levels of expression, you can tailor a perfect-fit access control system that evaluates in the safe realm of your server. All OCL rules use a few OCL operators but mostly names from your model that are probably in a ubiquitous language shared with the security officers of your domain. The transparency and fine-grained control of this access control system is precisely what many organizations need to protect their information and still allow for fast-paced development.
NOTE: This is the last chapter of The MDriven Book.
See also: AccessGroups,_InterestGroups_and_ViewModel-Enable, Access_groups