Hans Karlsen (talk | contribs) No edit summary |
No edit summary |
||
| (11 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
=== NEW - 30.09.2023 === | |||
New more generic way to access any API from the same place you logged in to with OpenIdConnect: [[OpenIdConnect access_token and refresh_token]] | |||
Office365 contains the GraphAPI | ===== Older information below ===== | ||
Background: https://learn.microsoft.com/en-us/graph/auth-v2-user | |||
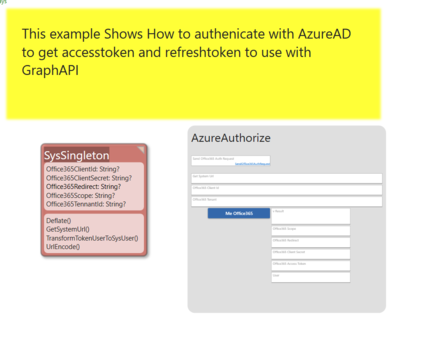
Office365 contains the GraphAPI used to access SharePoint documents, calendars, emails, etc. | |||
[[File:2023-04-24 17h45 47.png|none|thumb|422x422px]] | [[File:2023-04-24 17h45 47.png|none|thumb|422x422px]] | ||
What you need to do on the Azure side of this (also called the | What you need to do on the Azure side of this (also called the Tennant by Microsoft) is to do an App_Registration, do this at: https://Portal.Azure.com. | ||
From here you will need: | From here, you will need: | ||
* Client id, a guid string - put this in SysSingleton.Office365ClientId | |||
* Tennant id, a guid string - put this in SysSingleton.Office365TennantId | |||
* Client secret, SysSingleton.Office365ClientSecret | |||
You must also set up the redirect endpoints that shall be allowed for this solution (where Azure will go and is allowed to go in our app once it has done the authentication of the user). | |||
On Azure, give the EXACT SAME (case sensitive) as you put in SysSingleton.Office365Redirect. - this value MUST point to '''<your systems url>/Account/AzureAdAuthorize''' | |||
The Account/AzureAdAuthorize is a new controller action that assumes you have the above Office365 values in SysSingleton. It sends a post request to "<nowiki>https://login.microsoftonline.com/</nowiki>" + tennantid + "/oauth2/v2.0/token" and gets the accesstoken and the refreshtoken. These tokens are then written to CurrentUser - SysUser.Office365AccessToken and SysUser.Office365RefreshToken. | |||
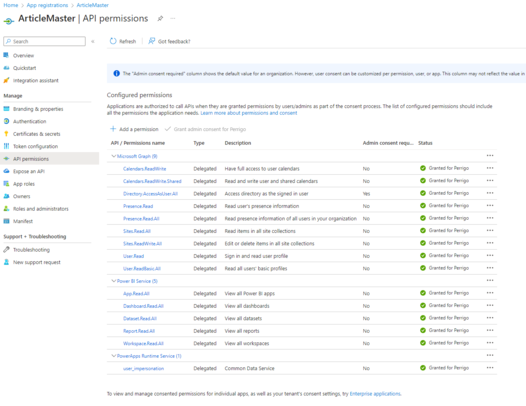
You will also need to Grant your app-registration access to particular interfaces in Office365 (allowed to see an email or not, allowed to see SharePoint lists or not). | |||
[[File:Image (3).png|none|thumb|526x526px]] | |||
Once you are ready to "log on" or authorize, you must say what scope THIS particular session should see: the scope looks like this, it's a space-delimited string: | |||
offline_access User.Read Sites.Read.All | |||
Other example: User.Read Directory.AccessAsUser.All Sites.Read.All | |||
Put this value in SysSingleton.Office365Scope. | |||
'''offline_access''' MUST be part of the scope to have Azure return the refreshtoken. If No refreshtoken is available, we cannot ask for new accesstokens. | |||
We can now formulate the request for (1) a code (lives a very short time) - we will then use this code to get (2) an access token (lives an hour) and (3) a refresh token (lives very long - often until revoked). | |||
We can now formulate the request for (1) a code (lives very short time) - we will then use this code to get | |||
'<nowiki>https://login.microsoftonline.com/'+SysSingleton.oclSingleton.Office365TennantId+'/oauth2/v2.0/authorize</nowiki>? | '<nowiki>https://login.microsoftonline.com/'+SysSingleton.oclSingleton.Office365TennantId+'/oauth2/v2.0/authorize</nowiki>? | ||
| Line 35: | Line 39: | ||
&scope='+SysSingleton.oclSingleton.UrlEncode( SysSingleton.oclSingleton.Office365Scope,false)+' | &scope='+SysSingleton.oclSingleton.UrlEncode( SysSingleton.oclSingleton.Office365Scope,false)+' | ||
&state='+SysSingleton.oclSingleton.UrlEncode('http://localhost:5020/App#/AzureAuthorize/$null$',false) | &state='+SysSingleton.oclSingleton.UrlEncode('http://localhost:5020/App#/AzureAuthorize/$null$',false) | ||
Note the last query parameter: state - | (The authentication must be done in a link sent from the browser since it will navigate to the provider for pwd etc - on return, we get the accesstoken and refreshtoken (if offline_acces scope is used)- later when we have the refreshtoken, we can silently ask for a new accesstoken that we can use with the API) | ||
Note the last query parameter: state - This is just round-tripped for us. We use it to know where to redirect once we have the accesstoken. | |||
You can use the Tagged value DataIsLink and have the above URL in a ViewModel column, or use the selfVM.NavigateURL in an action. | |||
Once you have the accesstoken, you can try a GraphAPI call like this: | |||
SysSingleton.oclSingleton.CurrentUser.Office365RefreshAccessToken; | |||
vResult:=selfVM.RestGet('<nowiki>https://graph.microsoft.com/v1.0/me','Bearer',SysSingleton.oclSingleton.CurrentUser.Office365AccessToken</nowiki>,<nowiki>''</nowiki>) | vResult:=selfVM.RestGet('<nowiki>https://graph.microsoft.com/v1.0/me','Bearer',SysSingleton.oclSingleton.CurrentUser.Office365AccessToken</nowiki>,<nowiki>''</nowiki>) | ||
{{Edited|July|12|2024}} | |||
[[Category:MDriven Turnkey]] | |||
[[Category:Authentication]] | |||
Latest revision as of 05:42, 19 March 2024
NEW - 30.09.2023
New more generic way to access any API from the same place you logged in to with OpenIdConnect: OpenIdConnect access_token and refresh_token
Older information below
Background: https://learn.microsoft.com/en-us/graph/auth-v2-user
Office365 contains the GraphAPI used to access SharePoint documents, calendars, emails, etc.
What you need to do on the Azure side of this (also called the Tennant by Microsoft) is to do an App_Registration, do this at: https://Portal.Azure.com.
From here, you will need:
- Client id, a guid string - put this in SysSingleton.Office365ClientId
- Tennant id, a guid string - put this in SysSingleton.Office365TennantId
- Client secret, SysSingleton.Office365ClientSecret
You must also set up the redirect endpoints that shall be allowed for this solution (where Azure will go and is allowed to go in our app once it has done the authentication of the user).
On Azure, give the EXACT SAME (case sensitive) as you put in SysSingleton.Office365Redirect. - this value MUST point to <your systems url>/Account/AzureAdAuthorize
The Account/AzureAdAuthorize is a new controller action that assumes you have the above Office365 values in SysSingleton. It sends a post request to "https://login.microsoftonline.com/" + tennantid + "/oauth2/v2.0/token" and gets the accesstoken and the refreshtoken. These tokens are then written to CurrentUser - SysUser.Office365AccessToken and SysUser.Office365RefreshToken.
You will also need to Grant your app-registration access to particular interfaces in Office365 (allowed to see an email or not, allowed to see SharePoint lists or not).
Once you are ready to "log on" or authorize, you must say what scope THIS particular session should see: the scope looks like this, it's a space-delimited string:
offline_access User.Read Sites.Read.All
Other example: User.Read Directory.AccessAsUser.All Sites.Read.All
Put this value in SysSingleton.Office365Scope.
offline_access MUST be part of the scope to have Azure return the refreshtoken. If No refreshtoken is available, we cannot ask for new accesstokens.
We can now formulate the request for (1) a code (lives a very short time) - we will then use this code to get (2) an access token (lives an hour) and (3) a refresh token (lives very long - often until revoked).
'https://login.microsoftonline.com/'+SysSingleton.oclSingleton.Office365TennantId+'/oauth2/v2.0/authorize?
client_id='+SysSingleton.oclSingleton.Office365ClientId+'
&response_type=code
&redirect_uri='+SysSingleton.oclSingleton.UrlEncode( SysSingleton.oclSingleton.Office365Redirect,false)+'
&response_mode=query
&scope='+SysSingleton.oclSingleton.UrlEncode( SysSingleton.oclSingleton.Office365Scope,false)+'
&state='+SysSingleton.oclSingleton.UrlEncode('http://localhost:5020/App#/AzureAuthorize/$null$',false)
(The authentication must be done in a link sent from the browser since it will navigate to the provider for pwd etc - on return, we get the accesstoken and refreshtoken (if offline_acces scope is used)- later when we have the refreshtoken, we can silently ask for a new accesstoken that we can use with the API)
Note the last query parameter: state - This is just round-tripped for us. We use it to know where to redirect once we have the accesstoken.
You can use the Tagged value DataIsLink and have the above URL in a ViewModel column, or use the selfVM.NavigateURL in an action.
Once you have the accesstoken, you can try a GraphAPI call like this:
SysSingleton.oclSingleton.CurrentUser.Office365RefreshAccessToken;
vResult:=selfVM.RestGet('https://graph.microsoft.com/v1.0/me','Bearer',SysSingleton.oclSingleton.CurrentUser.Office365AccessToken,'')